ACRYLICS
Advanced Cryptographic (Li) Capability-Based File System
ACRYLICS was developed as my master thesis.
It is a cryptographic file system which uses capabilities for access rights management but also as an active part of the encryption keys. This means that the file system is encrypted per user basis which are quite unique. It is not even possible for a user to know where to locate another users data.
Users can share files with each other by sharing a capability, hence the encryption information needed for another user to decrypt it.
The disk encryption scheme is based on Ivan Damgård and Kasper Dupont "Universally Composable Disk Encryption Schemes" (https://eprint.iacr.org/2005/333).
The capability model is based on Lanfranco Lopriore "Access right management by extended password capabilities" (https://link.springer.com/article/10.1007/s10207-017-0390-0)
Latest development is a ACRYLICS GUI manager for Linux where proof-of-concepts can be shown on a normal Linux system.
However ACRYLICS needs a fundamental different kernel-design to work. This is where QuasiOS comes into play.
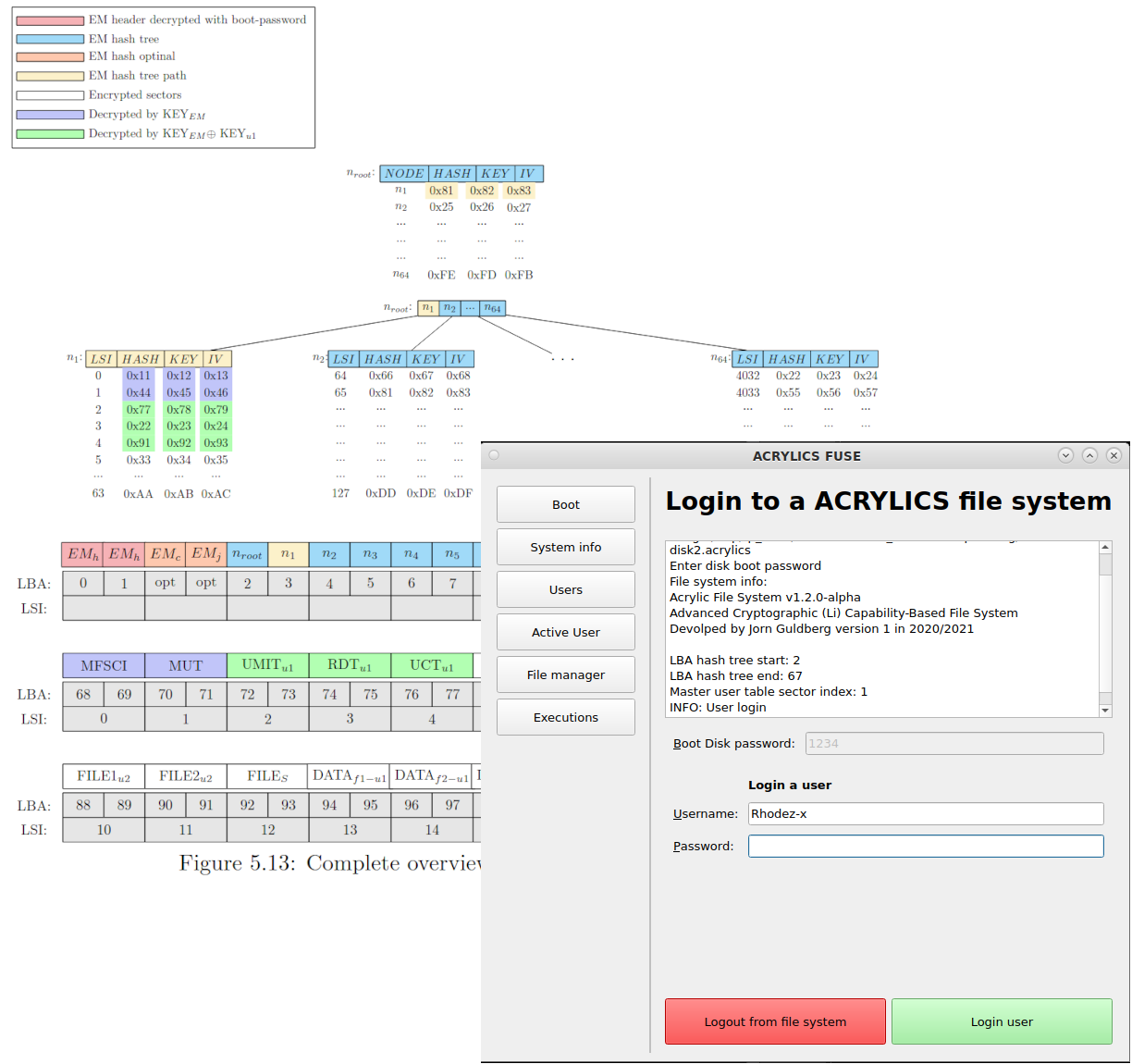
Above is an illustartion of the central tree structure which is used in ACRYLICS. In the master thesis it is explained how all the different password and encryption keys are managed. The tree is also a hash tree such that any unauthorised change on the disk will be noted and the user can be alerted that something is wrong.
ACRYLICS GUI Manager
The latest development is the GUI manager for Linux where ACRYLICS is about to be implemented with FUSE, such that it is possible to test out ACRYLICS and further development.
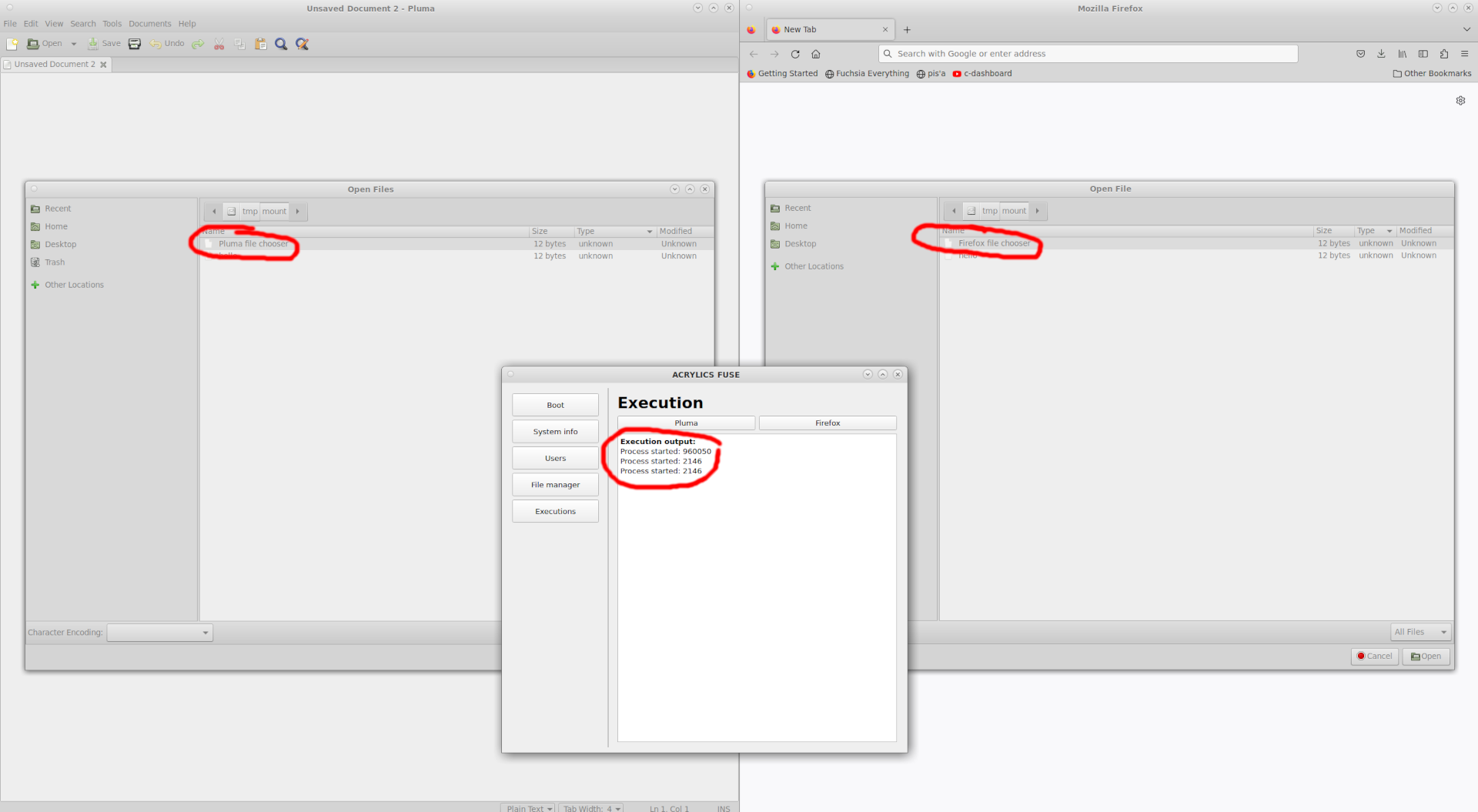
This is a short GIF which shows how two different users cannot see eachothers files. If one studied the raw bytes on the disk, it would be possible to see all the encrypted data with no change of decrypting anything else than what the user has permission for.
The next proof-of-concept on the way is to show how ACRYLICS also can be used to limit access for singel programs. Within the GUI Manager it is possible to execute programs in a special way.
This is the point where Linux and its kernel are limited to support ACRYLICS.
It is possible to track the PID of a spawned proccess from the GUI Manager and when a user is trying to access the folder where ACRYLICS is mounted via FUSE, the FUSE implementation can check which capabiliteis, hence encryption secrets the executed program knows.
So in this example we have tracked that the text editor "Pluma" is trying to access the folder and on the left-hand side it is firefox that is trying to access the folder, and they can only see what the user via ACRYLICS has granted the program to see.